Functions and structures for handling networkstatus documents as a client or as a directory cache. More...
#include "or.h"#include "bridges.h"#include "channel.h"#include "circuitmux.h"#include "circuitmux_ewma.h"#include "circuitstats.h"#include "config.h"#include "connection.h"#include "connection_or.h"#include "consdiffmgr.h"#include "control.h"#include "crypto_rand.h"#include "crypto_util.h"#include "directory.h"#include "dirserv.h"#include "dos.h"#include "entrynodes.h"#include "hibernate.h"#include "main.h"#include "microdesc.h"#include "networkstatus.h"#include "nodelist.h"#include "protover.h"#include "relay.h"#include "router.h"#include "routerlist.h"#include "routerparse.h"#include "scheduler.h"#include "transports.h"#include "torcert.h"#include "channelpadding.h"#include "voting_schedule.h"#include "dirauth/dirvote.h"#include "dirauth/mode.h"#include "dirauth/shared_random.h"
Data Structures | |
| struct | consensus_waiting_for_certs_t |
Macros | |
| #define | NETWORKSTATUS_PRIVATE |
| #define | N_CONSENSUS_BOOTSTRAP_SCHEDULES 2 |
| #define | CONSENSUS_BOOTSTRAP_SOURCE_AUTHORITY 0 |
| #define | CONSENSUS_BOOTSTRAP_SOURCE_ANY_DIRSERVER 1 |
| #define | NETWORKSTATUS_ALLOW_SKEW (24*60*60) |
| #define | AUTHORITY_NS_CACHE_INTERVAL (10*60) |
| #define | NONAUTHORITY_NS_CACHE_INTERVAL (60*60) |
| #define | DELAY_WHILE_FETCHING_CERTS (20*60) |
| #define | MIN_DELAY_FOR_FETCH_CERT_STATUS_FAILURE (1*60) |
| #define | CONSENSUS_MIN_SECONDS_BEFORE_CACHING 120 |
| #define | REASONABLY_LIVE_TIME (24*60*60) |
| #define | EARLY_CONSENSUS_NOTICE_SKEW 60 |
Typedefs | |
| typedef struct consensus_waiting_for_certs_t | consensus_waiting_for_certs_t |
Variables | |
| STATIC networkstatus_t * | current_ns_consensus = NULL |
| STATIC networkstatus_t * | current_md_consensus = NULL |
Detailed Description
Functions and structures for handling networkstatus documents as a client or as a directory cache.
A consensus networkstatus object is created by the directory authorities. It authenticates a set of network parameters–most importantly, the list of all the relays in the network. This list of relays is represented as an array of routerstatus_t objects.
There are currently two flavors of consensus. With the older "NS" flavor, each relay is associated with a digest of its router descriptor. Tor instances that use this consensus keep the list of router descriptors as routerinfo_t objects stored and managed in routerlist.c. With the newer "microdesc" flavor, each relay is associated with a digest of the microdescriptor that the authorities made for it. These are stored and managed in microdesc.c. Information about the router is divided between the the networkstatus and the microdescriptor according to the general rule that microdescriptors should hold information that changes much less frequently than the information in the networkstatus.
Modern clients use microdescriptor networkstatuses. Directory caches need to keep both kinds of networkstatus document, so they can serve them.
This module manages fetching, holding, storing, updating, and validating networkstatus objects. The download-and-validate process is slightly complicated by the fact that the keys you need to validate a consensus are stored in the authority certificates, which you might not have yet when you download the consensus.
Macro Definition Documentation
◆ AUTHORITY_NS_CACHE_INTERVAL
| #define AUTHORITY_NS_CACHE_INTERVAL (10*60) |
How frequently do directory authorities re-download fresh networkstatus documents?
◆ CONSENSUS_MIN_SECONDS_BEFORE_CACHING
| #define CONSENSUS_MIN_SECONDS_BEFORE_CACHING 120 |
How long do we (as a cache) wait after a consensus becomes non-fresh before trying to fetch another?
◆ DELAY_WHILE_FETCHING_CERTS
| #define DELAY_WHILE_FETCHING_CERTS (20*60) |
How long will we hang onto a possibly live consensus for which we're fetching certs before we check whether there is a better one?
◆ MIN_DELAY_FOR_FETCH_CERT_STATUS_FAILURE
| #define MIN_DELAY_FOR_FETCH_CERT_STATUS_FAILURE (1*60) |
What is the minimum time we need to have waited fetching certs, before we increment the consensus download schedule on failure?
◆ NETWORKSTATUS_ALLOW_SKEW
| #define NETWORKSTATUS_ALLOW_SKEW (24*60*60) |
How far in the future do we allow a network-status to get before removing it? (seconds)
◆ NONAUTHORITY_NS_CACHE_INTERVAL
| #define NONAUTHORITY_NS_CACHE_INTERVAL (60*60) |
How frequently do non-authority directory caches re-download fresh networkstatus documents?
Typedef Documentation
◆ consensus_waiting_for_certs_t
| typedef struct consensus_waiting_for_certs_t consensus_waiting_for_certs_t |
A v3 consensus networkstatus that we've received, but which we don't have enough certificates to be happy about.
Function Documentation
◆ client_would_use_router()
| int client_would_use_router | ( | const routerstatus_t * | rs, |
| time_t | now | ||
| ) |
Return 0 if this routerstatus is obsolete, too new, isn't running, or otherwise not a descriptor that we would make any use of even if we had it. Else return 1.
◆ compare_digest_to_routerstatus_entry()
| int compare_digest_to_routerstatus_entry | ( | const void * | _key, |
| const void ** | _member | ||
| ) |
Helper for bsearching a list of routerstatus_t pointers: compare a digest in the key to the identity digest of a routerstatus_t.
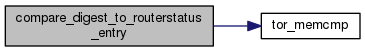
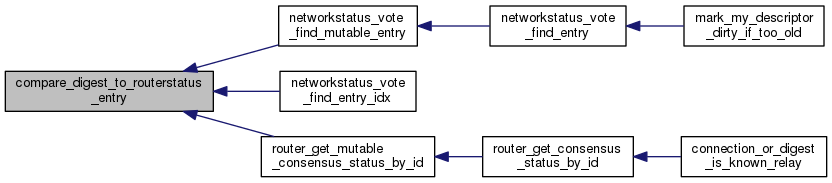
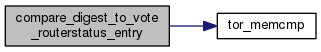
◆ compare_digest_to_vote_routerstatus_entry()
| int compare_digest_to_vote_routerstatus_entry | ( | const void * | _key, |
| const void ** | _member | ||
| ) |
Helper for bsearching a list of routerstatus_t pointers: compare a digest in the key to the identity digest of a routerstatus_t.
◆ consensus_is_waiting_for_certs()
| int consensus_is_waiting_for_certs | ( | void | ) |
Return 1 if we have a consensus but we don't have enough certificates to start using it yet.
◆ document_signature_dup()
| document_signature_t* document_signature_dup | ( | const document_signature_t * | sig | ) |
Return a newly allocated copy of sig
◆ document_signature_free_()
| void document_signature_free_ | ( | document_signature_t * | sig | ) |
Free all storage held in sig
◆ getinfo_helper_networkstatus()
| int getinfo_helper_networkstatus | ( | control_connection_t * | conn, |
| const char * | question, | ||
| char ** | answer, | ||
| const char ** | errmsg | ||
| ) |
If question is a string beginning with "ns/" in a format the control interface expects for a GETINFO question, set *answer to a newly-allocated string containing networkstatus lines for the appropriate ORs. Return 0 on success, -1 on unrecognized question format.
◆ MOCK_IMPL() [1/12]
| MOCK_IMPL | ( | routerstatus_t * | , |
| router_get_mutable_consensus_status_by_descriptor_digest | , | ||
| ( networkstatus_t *consensus, const char *digest) | |||
| ) |
As router_get_consensus_status_by_descriptor_digest, but does not return a const pointer.
◆ MOCK_IMPL() [2/12]
| MOCK_IMPL | ( | smartlist_t * | , |
| router_get_descriptor_digests | , | ||
| (void) | |||
| ) |
Return a smartlist of all router descriptor digests in the current consensus
◆ MOCK_IMPL() [3/12]
| MOCK_IMPL | ( | download_status_t * | , |
| router_get_dl_status_by_descriptor_digest | , | ||
| (const char *d) | |||
| ) |
Given the digest of a router descriptor, return its current download status, or NULL if the digest is unrecognized.
◆ MOCK_IMPL() [4/12]
| MOCK_IMPL | ( | download_status_t * | , |
| networkstatus_get_dl_status_by_flavor | , | ||
| (consensus_flavor_t flavor) | |||
| ) |
Look up the currently active (depending on bootstrap status) download status for this consensus flavor and return a pointer to it.
◆ MOCK_IMPL() [5/12]
| MOCK_IMPL | ( | download_status_t * | , |
| networkstatus_get_dl_status_by_flavor_bootstrap | , | ||
| (consensus_flavor_t flavor) | |||
| ) |
Look up the bootstrap download status for this consensus flavor and return a pointer to it.
◆ MOCK_IMPL() [6/12]
| MOCK_IMPL | ( | download_status_t * | , |
| networkstatus_get_dl_status_by_flavor_running | , | ||
| (consensus_flavor_t flavor) | |||
| ) |
Look up the running (non-bootstrap) download status for this consensus flavor and return a pointer to it.
◆ MOCK_IMPL() [7/12]
| MOCK_IMPL | ( | networkstatus_t * | , |
| networkstatus_get_latest_consensus | , | ||
| (void) | |||
| ) |
Return the most recent consensus that we have downloaded, or NULL if we don't have one.
◆ MOCK_IMPL() [8/12]
| MOCK_IMPL | ( | networkstatus_t * | , |
| networkstatus_get_latest_consensus_by_flavor | , | ||
| (consensus_flavor_t f) | |||
| ) |
Return the latest consensus we have whose flavor matches f, or NULL if we don't have one.
◆ MOCK_IMPL() [9/12]
| MOCK_IMPL | ( | networkstatus_t * | , |
| networkstatus_get_live_consensus | , | ||
| (time_t now) | |||
| ) |
Return the most recent consensus that we have downloaded, or NULL if it is no longer live.
◆ MOCK_IMPL() [10/12]
| MOCK_IMPL | ( | int | , |
| networkstatus_consensus_is_bootstrapping | , | ||
| (time_t now) | |||
| ) |
Check if we need to download a consensus during tor's bootstrap phase. If we have no consensus, or our consensus is unusably old, return 1. As soon as we have received a consensus, return 0, even if we don't have enough certificates to validate it. If a fallback directory gives us a consensus we can never get certs for, check_consensus_waiting_for_certs() will wait 20 minutes before failing the cert downloads. After that, a new consensus will be fetched from a randomly chosen fallback.
◆ MOCK_IMPL() [11/12]
| MOCK_IMPL | ( | int | , |
| networkstatus_consensus_can_use_extra_fallbacks | , | ||
| (const or_options_t *options) | |||
| ) |
Check if we can use fallback directory mirrors for a consensus download. If we have fallbacks and don't want to fetch from the authorities, we can use them.
◆ MOCK_IMPL() [12/12]
| MOCK_IMPL | ( | int32_t | , |
| networkstatus_get_param | , | ||
| (const networkstatus_t *ns, const char *param_name, int32_t default_val, int32_t min_val, int32_t max_val) | |||
| ) |
Return the value of a integer parameter from the networkstatus ns whose name is param_name. If ns is NULL, try loading the latest consensus ourselves. Return default_val if no latest consensus, or if it has no parameter called param_name. Make sure the value parsed from the consensus is at least min_val and at most max_val and raise/cap the parsed value if necessary.
◆ networkstatus_check_consensus_signature()
| int networkstatus_check_consensus_signature | ( | networkstatus_t * | consensus, |
| int | warn | ||
| ) |
Given a v3 networkstatus consensus in consensus, check every as-yet-unchecked signature on consensus. Return 1 if there is a signature from every recognized authority on it, 0 if there are enough good signatures from recognized authorities on it, -1 if we might get enough good signatures by fetching missing certificates, and -2 otherwise. Log messages at INFO or WARN: if warn is over 1, warn about every problem; if warn is at least 1, warn only if we can't get enough signatures; if warn is negative, log nothing at all.
◆ networkstatus_check_document_signature()
| int networkstatus_check_document_signature | ( | const networkstatus_t * | consensus, |
| document_signature_t * | sig, | ||
| const authority_cert_t * | cert | ||
| ) |
Check whether the signature sig is correctly signed with the signing key in cert. Return -1 if cert doesn't match the signing key; otherwise set the good_signature or bad_signature flag on voter, and return 0.
◆ networkstatus_consensus_can_use_multiple_directories()
| int networkstatus_consensus_can_use_multiple_directories | ( | const or_options_t * | options | ) |
Check if we can use multiple directories for a consensus download. Only clients (including bridge relays, which act like clients) benefit from multiple simultaneous consensus downloads.
◆ networkstatus_consensus_download_failed()
| void networkstatus_consensus_download_failed | ( | int | status_code, |
| const char * | flavname | ||
| ) |
Called when an attempt to download a consensus fails: note that the failure occurred, and possibly retry.
◆ networkstatus_consensus_reasonably_live()
| int networkstatus_consensus_reasonably_live | ( | const networkstatus_t * | consensus, |
| time_t | now | ||
| ) |
Determine if consensus is valid or expired recently enough that we can still use it.
Return 1 if the consensus is reasonably live, or 0 if it is too old.
◆ networkstatus_dump_bridge_status_to_file()
| void networkstatus_dump_bridge_status_to_file | ( | time_t | now | ) |
Write out router status entries for all our bridge descriptors.
◆ networkstatus_free_all()
| void networkstatus_free_all | ( | void | ) |
Free all storage held locally in this module.
◆ networkstatus_get_bw_weight()
| int32_t networkstatus_get_bw_weight | ( | networkstatus_t * | ns, |
| const char * | weight_name, | ||
| int32_t | default_val | ||
| ) |
Return the value of a integer bw weight parameter from the networkstatus ns whose name is weight_name. If ns is NULL, try loading the latest consensus ourselves. Return default_val if no latest consensus, or if it has no parameter called weight_name.
◆ networkstatus_get_flavor_name()
| const char* networkstatus_get_flavor_name | ( | consensus_flavor_t | flav | ) |
Return the name of the consensus flavor flav as used to identify the flavor in directory documents.
◆ networkstatus_get_overridable_param()
| int32_t networkstatus_get_overridable_param | ( | const networkstatus_t * | ns, |
| int32_t | torrc_value, | ||
| const char * | param_name, | ||
| int32_t | default_val, | ||
| int32_t | min_val, | ||
| int32_t | max_val | ||
| ) |
As networkstatus_get_param(), but check torrc_value before checking the consensus. If torrc_value is in-range, then return it instead of the value from the consensus.
◆ networkstatus_get_reasonably_live_consensus()
| networkstatus_t* networkstatus_get_reasonably_live_consensus | ( | time_t | now, |
| int | flavor | ||
| ) |
As networkstatus_get_live_consensus(), but is way more tolerant of expired consensuses.
◆ networkstatus_get_voter_by_id()
| networkstatus_voter_info_t* networkstatus_get_voter_by_id | ( | networkstatus_t * | vote, |
| const char * | identity | ||
| ) |
Return the voter info from vote for the voter whose identity digest is identity, or NULL if no such voter is associated with vote.
◆ networkstatus_get_voter_sig_by_alg()
| document_signature_t* networkstatus_get_voter_sig_by_alg | ( | const networkstatus_voter_info_t * | voter, |
| digest_algorithm_t | alg | ||
| ) |
Return the signature made by voter using the algorithm alg, or NULL if none is found.
◆ networkstatus_get_weight_scale_param()
| int networkstatus_get_weight_scale_param | ( | networkstatus_t * | ns | ) |
Retrieve the consensus parameter that governs the fixed-point precision of our network balancing 'bandwidth-weights' (which are themselves integer consensus values). We divide them by this value and ensure they never exceed this value.
◆ networkstatus_getinfo_by_purpose()
| char* networkstatus_getinfo_by_purpose | ( | const char * | purpose_string, |
| time_t | now | ||
| ) |
Alloc and return a string describing routerstatuses for the most recent info of each router we know about that is of purpose purpose_string. Return NULL if unrecognized purpose.
Right now this function is oriented toward listing bridges (you shouldn't use this for general-purpose routers, since those should be listed from the consensus, not from the routers list).
◆ networkstatus_getinfo_helper_single()
| char* networkstatus_getinfo_helper_single | ( | const routerstatus_t * | rs | ) |
Generate networkstatus lines for a single routerstatus_t object, and return the result in a newly allocated string. Used only by controller interface (for now.)
◆ networkstatus_is_live()
| int networkstatus_is_live | ( | const networkstatus_t * | ns, |
| time_t | now | ||
| ) |
Given a consensus in ns, return true iff currently live and unexpired.
◆ networkstatus_note_certs_arrived()
| void networkstatus_note_certs_arrived | ( | const char * | source_dir | ) |
Called when we have gotten more certificates: see whether we can now verify a pending consensus.
If source_dir is non-NULL, it's the identity digest for a directory that we've just successfully retrieved certificates from, so try it first to fetch any missing certificates.
◆ networkstatus_parse_flavor_name()
| int networkstatus_parse_flavor_name | ( | const char * | flavname | ) |
Return the consensus_flavor_t value for the flavor called flavname, or -1 if the flavor is not recognized.
◆ networkstatus_read_cached_consensus()
| char* networkstatus_read_cached_consensus | ( | const char * | flavorname | ) |
Return a new string containing the current cached consensus of flavor flavorname.
◆ networkstatus_reset_download_failures()
| void networkstatus_reset_download_failures | ( | void | ) |
Reset the descriptor download failure count on all networkstatus docs, so that we can retry any long-failed documents immediately.
◆ networkstatus_reset_warnings()
| void networkstatus_reset_warnings | ( | void | ) |
Forget that we've warned about anything networkstatus-related, so we will give fresh warnings if the same behavior happens again.
◆ networkstatus_set_current_consensus()
| int networkstatus_set_current_consensus | ( | const char * | consensus, |
| const char * | flavor, | ||
| unsigned | flags, | ||
| const char * | source_dir | ||
| ) |
Try to replace the current cached v3 networkstatus with the one in consensus. If we don't have enough certificates to validate it, store it in consensus_waiting_for_certs and launch a certificate fetch.
If flags & NSSET_FROM_CACHE, this networkstatus has come from the disk cache. If flags & NSSET_WAS_WAITING_FOR_CERTS, this networkstatus was already received, but we were waiting for certificates on it. If flags & NSSET_DONT_DOWNLOAD_CERTS, do not launch certificate downloads as needed. If flags & NSSET_ACCEPT_OBSOLETE, then we should be willing to take this consensus, even if it comes from many days in the past.
If source_dir is non-NULL, it's the identity digest for a directory that we've just successfully retrieved a consensus or certificates from, so try it first to fetch any missing certificates.
Return 0 on success, <0 on failure. On failure, caller should increment the failure count as appropriate.
We return -1 for mild failures that don't need to be reported to the user, and -2 for more serious problems.
◆ networkstatus_valid_until_is_reasonably_live()
| int networkstatus_valid_until_is_reasonably_live | ( | time_t | valid_until, |
| time_t | now | ||
| ) |
As networkstatus_consensus_reasonably_live, but takes a valid_until time rather than an entire consensus.
◆ networkstatus_vote_find_entry()
| const routerstatus_t* networkstatus_vote_find_entry | ( | networkstatus_t * | ns, |
| const char * | digest | ||
| ) |
Return the entry in ns for the identity digest digest, or NULL if none was found.
◆ networkstatus_vote_find_entry_idx()
| int networkstatus_vote_find_entry_idx | ( | networkstatus_t * | ns, |
| const char * | digest, | ||
| int * | found_out | ||
| ) |
Search the routerstatuses in ns for one whose identity digest is digest. Return value and set *found_out as for smartlist_bsearch_idx().
◆ networkstatus_vote_find_mutable_entry()
| routerstatus_t* networkstatus_vote_find_mutable_entry | ( | networkstatus_t * | ns, |
| const char * | digest | ||
| ) |
As networkstatus_find_entry, but do not return a const pointer

◆ networkstatus_vote_free_()
| void networkstatus_vote_free_ | ( | networkstatus_t * | ns | ) |
Free all storage held in ns.
◆ ns_detached_signatures_free_()
| void ns_detached_signatures_free_ | ( | ns_detached_signatures_t * | s | ) |
Release all storage held in s.
◆ router_get_consensus_status_by_descriptor_digest()
| const routerstatus_t* router_get_consensus_status_by_descriptor_digest | ( | networkstatus_t * | consensus, |
| const char * | digest | ||
| ) |
Return the consensus view of the status of the router whose current descriptor digest in consensus is digest, or NULL if no such router is known.
◆ router_get_consensus_status_by_id()
| const routerstatus_t* router_get_consensus_status_by_id | ( | const char * | digest | ) |
Return the consensus view of the status of the router whose identity digest is digest, or NULL if we don't know about any such router.
◆ router_get_mutable_consensus_status_by_id()
| routerstatus_t* router_get_mutable_consensus_status_by_id | ( | const char * | digest | ) |
As router_get_consensus_status_by_id, but do not return a const pointer

◆ router_reload_consensus_networkstatus()
| int router_reload_consensus_networkstatus | ( | void | ) |
Read every cached v3 consensus networkstatus from the disk.
◆ routers_update_all_from_networkstatus()
| void routers_update_all_from_networkstatus | ( | time_t | now, |
| int | dir_version | ||
| ) |
If the network-status list has changed since the last time we called this function, update the status of every routerinfo from the network-status list. If dir_version is 2, it's a v2 networkstatus that changed. If dir_version is 3, it's a v3 consensus that changed.
◆ routers_update_status_from_consensus_networkstatus()
| void routers_update_status_from_consensus_networkstatus | ( | smartlist_t * | routers, |
| int | reset_failures | ||
| ) |
Given a list routers of routerinfo_t *, update each status field according to our current consensus networkstatus. May re-order routers.

◆ routerstatus_free_()
| void routerstatus_free_ | ( | routerstatus_t * | rs | ) |
Free all storage held by the routerstatus object rs.
◆ should_delay_dir_fetches()
| int should_delay_dir_fetches | ( | const or_options_t * | options, |
| const char ** | msg_out | ||
| ) |
Return 1 if there's a reason we shouldn't try any directory fetches yet (e.g. we demand bridges and none are yet known). Else return 0.
If we return 1 and msg_out is provided, set msg_out to an explanation of why directory fetches are delayed. (If we return 0, we set msg_out to NULL.)
◆ signed_descs_update_status_from_consensus_networkstatus()
| void signed_descs_update_status_from_consensus_networkstatus | ( | smartlist_t * | descs | ) |
Given a list of signed_descriptor_t, update their fields (mainly, when they were last listed) from the most recent consensus.
◆ update_certificate_downloads()
| void update_certificate_downloads | ( | time_t | now | ) |
Launch requests as appropriate for missing directory authority certificates.
◆ update_consensus_networkstatus_fetch_time()
| void update_consensus_networkstatus_fetch_time | ( | time_t | now | ) |
Update the time at which we'll consider replacing the current consensus of flavor 'flavor'
◆ update_networkstatus_downloads()
| void update_networkstatus_downloads | ( | time_t | now | ) |
Launch requests for networkstatus documents as appropriate. This is called when we retry all the connections on a SIGHUP and periodically by a Periodic event which checks whether we want to download any networkstatus documents.
Launch a consensus download request, we will wait for the consensus to download and when it completes we will launch a certificate download request.
◆ vote_routerstatus_free_()
| void vote_routerstatus_free_ | ( | vote_routerstatus_t * | rs | ) |
Free all storage held by the vote_routerstatus object rs.
◆ warn_early_consensus()
| STATIC void warn_early_consensus | ( | const networkstatus_t * | c, |
| const char * | flavor, | ||
| time_t | now | ||
| ) |
Check whether we received a consensus that appears to be coming from the future. Because we implicitly trust the directory authorities' idea of the current time, we produce a warning if we get an early consensus.
If we got a consensus that is time stamped far in the past, that could simply have come from a stale cache. Possible ways to get a consensus from the future can include:
- enough directory authorities have wrong clocks
- directory authorities collude to produce misleading time stamps
- our own clock is wrong (this is by far the most likely)
We neglect highly improbable scenarios that involve actual time travel.
If a consensus appears more than this many seconds before it could possibly be a sufficiently-signed consensus, declare that our clock is skewed.
◆ we_want_to_fetch_flavor()
| int we_want_to_fetch_flavor | ( | const or_options_t * | options, |
| int | flavor | ||
| ) |
Return true iff, given the options listed in options, flavor is the flavor of a consensus networkstatus that we would like to fetch.
For certificate fetches, use we_want_to_fetch_unknown_auth_certs, and for serving fetched documents, use directory_caches_dir_info.
◆ we_want_to_fetch_unknown_auth_certs()
| int we_want_to_fetch_unknown_auth_certs | ( | const or_options_t * | options | ) |
Return true iff, given the options listed in options, we would like to fetch and store unknown authority certificates.
For consensus and descriptor fetches, use we_want_to_fetch_flavor, and for serving fetched certificates, use directory_caches_unknown_auth_certs.

Variable Documentation
◆ current_md_consensus
| STATIC networkstatus_t* current_md_consensus = NULL |
Most recently received and validated v3 "microdesc"-flavored consensus network status.
◆ current_ns_consensus
| STATIC networkstatus_t* current_ns_consensus = NULL |
Most recently received and validated v3 "ns"-flavored consensus network status.
 1.8.13
1.8.13